
Several organizations in the shipping and logistics, media and entertainment, technology, and automotive sectors in Italy, Spain, Taiwan, Thailand, Türkiye, and the U.K. have been targeted by the China-based hacking group APT41, as part of a "sustained campaign" of cyberattacks.
According to a report published by Google-owned Mandiant on Thursday, APT41 successfully infiltrated and maintained unauthorized access to numerous networks since 2023, allowing the extraction of sensitive data over an extended period.
The attacks carried out by APT41, also known by aliases such as Barium, Wicked Panda, and Winnti, highlight their ability to maintain covert operations over extended periods.
Mandiant highlighted the uniqueness of APT41 among China-nexus actors due to its use of "non-public malware typically reserved for espionage operations in activities that appear to fall outside the scope of state-sponsored missions."
The technical report also reveals APT41's reconnaissance activities targeting similar sectors in Singapore, suggesting a potential expansion of their attack vectors. This indicates an increased threat to other regions and industries.
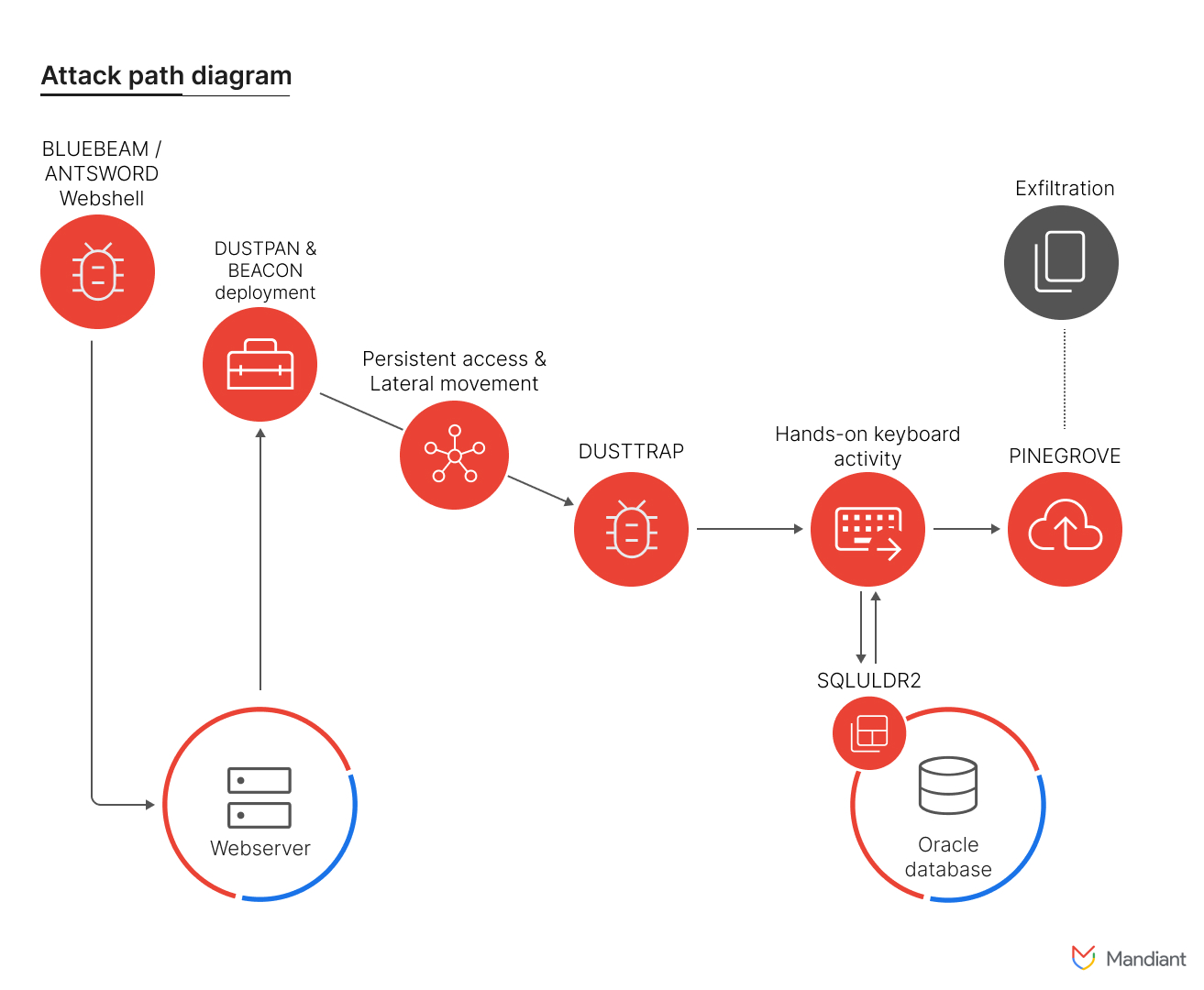
APT41 is known for its dual-role operations, combining state-sponsored espionage with financially motivated intrusions. Their espionage activities focus on health care, high-tech, telecommunications, economically significant sectors, and sophisticated attack techniques.
Recent attacks have showcased APT41's sophisticated methods:
Mandiant has published indicators of compromise and forensic data to aid organizations in identifying and mitigating APT41 infections.
APT41’s hacking activities span over a decade, impacting thousands of organizations worldwide, including software and video gaming companies, governments, universities, think tanks, non-profits, and pro-democracy figures in Hong Kong.
Their operations extend across multiple countries, including the United States, Australia, Brazil, Chile, India, Indonesia, Japan, Malaysia, Pakistan, Singapore, South Korea, Taiwan, Thailand, and Vietnam.
In response to these activities, the U.S. Department of Justice has charged several Chinese nationals – Zhang Haoran, Tan Dailin, Jiang Lizhi, Qian Chuan, and Fu Qiang – linking them to APT41's hacking operations.